|
Boost : |
From: Bhuyan, Jyotideep (JyotideepBhuyan_at_[hidden])
Date: 2024-06-27 07:25:51
Hi Seth,
Boost list run by bdawes at acm.org, gregod at cs.rpi.edu, cpdaniel at pacbell.net, john at johnmaddock.co.uk
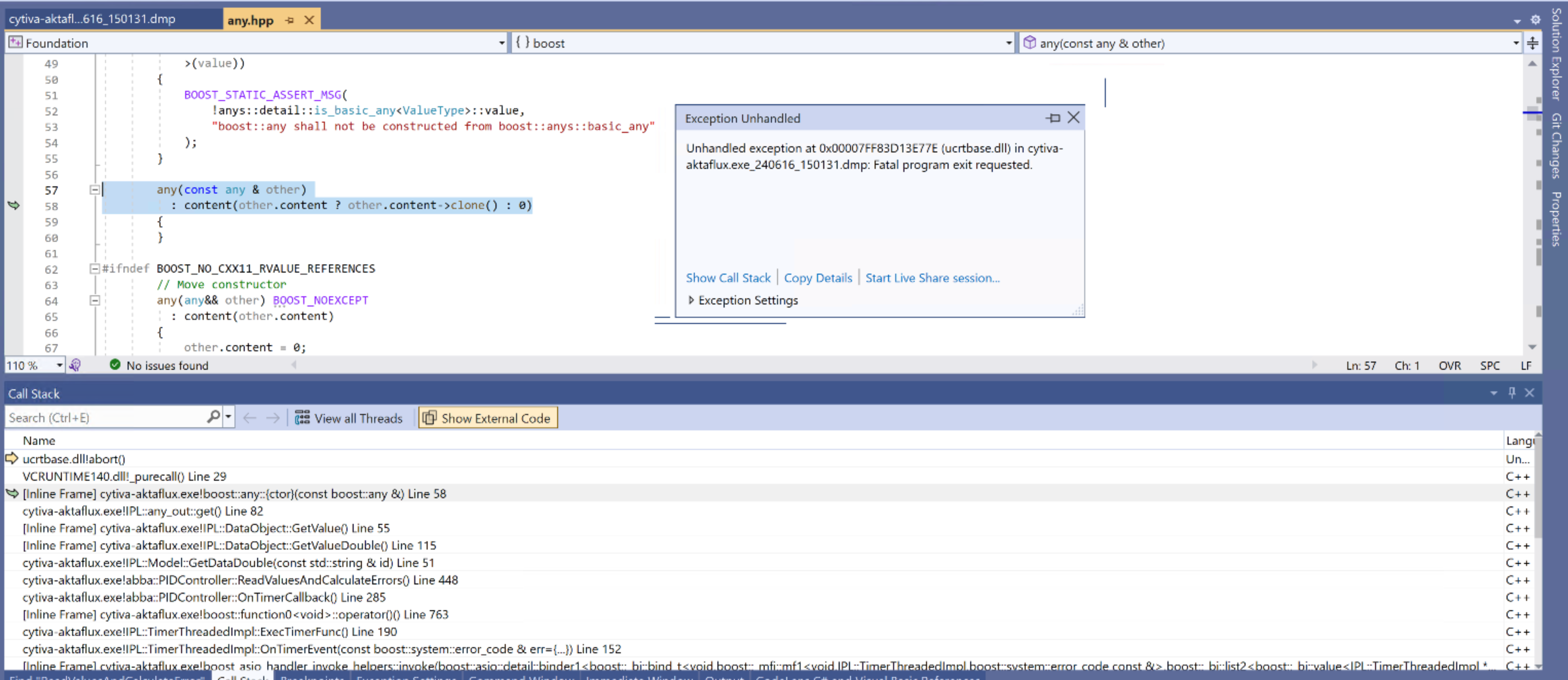
Further investigating on the same line as you have pointed out, We could see in the call stack it is pointing to any.hpp (Boost version 1.78 ) clone() function which is a pure virtual method. It is causing a crash since it is leading to the call __purecall() method of ucrtbase.dll (windows 10) which in turn calls the abort method to terminate the process.
Can you please advise on how to resolve this issue?
Additionally, just wanted to understand why a pure virtual method call is happening from the constructor.
[cid:image001.png_at_01DAC891.53E09050]
Best Regards,
Jyotideep (JD)
Confidential - Company Proprietary
From: Boost <boost-bounces_at_[hidden]> On Behalf Of Seth via Boost
Sent: Tuesday, June 25, 2024 6:09 AM
To: Boost List <boost_at_[hidden]>
Cc: Seth <bugs_at_[hidden]>
Subject: Re: [boost] Application crash due to boost
Looks like a crash due to undefined behavior. Apparently ReportWarningPumpController: : abba leads to invocation of a pure virtual function call. This usually indicates that a pointer is stale or refers to an instance of a virtual type that is
ZjQcmQRYFpfptBannerStart
This Message Is From an External Sender
This message came from outside your organization. Use caution when opening.
ZjQcmQRYFpfptBannerEnd
Looks like a crash due to undefined behavior. Apparently ReportWarningPumpController::abba leads to invocation of a pure virtual function call.
This usually indicates that a pointer is stale or refers to an instance of a virtual type that is not yet / no longer fully constructed.
This, in turn seems to happen in response to an `std::underflow_error` being thrown. The standard library components do not throw this exception (mathematical functions report underflow errors as specified in https://urldefense.com/v3/__https://en.cppreference.com/w/cpp/numeric/math/math_errhandling__;!!G8Er-fQLpA!PFdqC80cipChB5rIkDH1aktGE0i6XEEjdFsAZu85skLdRBti21XVgU7V68UMon1l2Z7yNyDxDNa4EfQgPSmPlBno$
That likely makes this an application domain bug. Or it should give you information to reduce to a minimal reproducer that leads to the exception being raised in case you think it is raised in error.
More analysis will be pretty hard without source code.
Hope this helps,
Seth
On Tue, Jun 18, 2024, at 2:55 PM, Bhuyan, Jyotideep via Boost wrote:
> Hi,
> My application uses the boost version of 1.78. and it crashes after
> running for approximately 2 hours. When I created the dump file, I saw
> the below exceptions. Can anyone share some insight into what is
> happening here? How to debug and fix this issue?
>
>
> EXCEPTION_RECORD: (.exr -1)
> ExceptionAddress: 00007ffc2fece77e (ucrtbase!abort+0x000000000000004e)
> ExceptionCode: c0000409 (Security check failure or stack buffer overrun)
> ExceptionFlags: 00000001
> NumberParameters: 1
> Parameter[0]: 0000000000000007
> Subcode: 0x7 FAST_FAIL_FATAL_APP_EXIT
>
> PROCESS_NAME: cytiva-aktaflux.exe
>
> ERROR_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a
> stack-based buffer in this application. This overrun could potentially
> allow a malicious user to gain control of this application.
>
> EXCEPTION_CODE_STR: c0000409
>
> EXCEPTION_PARAMETER1: 0000000000000007
>
> FAULTING_THREAD: 00000d2c
>
> STACK_TEXT:
> 00000069`f24fe7a0 00007ffc`220a6c4a : 00007ff6`00000003
> 000001b4`00000003 00000069`f24fe860 00007ff6`33cc181f :
> ucrtbase!abort+0x4e
> 00000069`f24fe7d0 00007ff6`33c41272 : 00000069`f24ff180
> 00000000`00000000 00000069`00000001 000001b4`301fc3d8 :
> VCRUNTIME140!_purecall+0x1a
> 00000069`f24fe800 00007ff6`33cc2d42 : 000001b4`301ff8c0
> 00000069`f24fe890 00000069`f24fe9d0 00000000`ffffffff :
> cytiva_aktaflux!ILT+131690(?ReportWarningPumpControllerabbaEEAAXAEBV?$basic_stringDU?$char_traitsDstdV?$allocatorD+0x3
> 00000069`f24fe840 00007ff6`33dc38ad : 00000069`f24fe9d0
> 000001b4`301ff8c0 000001b4`4a725560 0000a9ff`85eb46dc :
> cytiva_aktaflux!boost::system::detail::system_category_message_win32+0x1b2
> 00000069`f24fe890 00007ff6`33dc2b22 : 000001b4`301ff8c0
> 00000000`ffffffff 000001b4`301ff8c0 00000000`ffffffff :
> cytiva_aktaflux!boost::date_time::microsec_clock<boost::posix_time::ptime>::create_time+0xfd
> 00000069`f24fe8d0 00007ff6`33cb9655 : 000001b4`4d1f8b40
> 000001b4`4d1f8b40 00000000`00000000 00000000`00000001 :
> cytiva_aktaflux!std::_Tree<std::_Tmap_traits<unsigned
> short,ViewDebugRegisterValuesFrame::RegisterTrack,std::less<unsigned
> short>,std::allocator<std::pair<unsigned short const
> ,ViewDebugRegisterValuesFrame::RegisterTrack> >,0> >::clear+0x72
> 00000069`f24fef90 00007ff6`33cb922d : 000001b4`4d1f8b78
> 000001b4`4d1f8b78 000001b4`4d1f8b40 0000000f`042da045 :
> cytiva_aktaflux!boost::exception_detail::clone_impl<boost::exception_detail::bad_alloc_>::clone+0xa5
> 00000069`f24ff060 00007ff6`33cbb200 : 00000069`f24ff1b0
> 00000000`00000000 000001b4`4ef19a80 00000069`f24ff3b0 :
> cytiva_aktaflux!std::basic_string<char,std::char_traits<char>,std::allocator<char>
> >::begin+0xd
> 00000069`f24ff130 00007ff6`33cb16ff : 000001b4`4d4138f0
> 00000000`00000001 00000000`00000000 000001b4`4d4138f0 :
> cytiva_aktaflux!boost::system::error_code::equals+0x120
> 00000069`f24ff220 00007ff6`33cb1144 : 00000000`00000000
> 00000069`00000000 00000069`f24ff3b0 00000069`f24ff510 :
> cytiva_aktaflux!boost::exception_detail::clone_impl<boost::exception_detail::bad_exception_>::clone_impl<boost::exception_detail::bad_exception_>+0xaf
> 00000069`f24ff370 00007ff6`33cb2c4a : 00000000`00000000
> 00000000`ffffffff 00000000`00000000 000001b4`4d25dd10 :
> cytiva_aktaflux!std::basic_string<char,std::char_traits<char>,std::allocator<char>
> >::basic_string<char,std::char_traits<char>,std::allocator<char> >+0x34
> 00000069`f24ff450 00007ff6`33cb2403 : 00000000`406d1388
> 000001b4`4d208718 000001b4`4d2086a0 00000000`00000000 :
> cytiva_aktaflux!std::bad_exception::bad_exception+0x3a
> 00000069`f24ffab0 00007ff6`33c70cd4 : 000001b4`4d208730
> 000001b4`4d208718 000001b4`4d2086a0 00000000`00000000 :
> cytiva_aktaflux!boost::wrapexcept<boost::property_tree::ptree_bad_path>::wrapexcept<boost::property_tree::ptree_bad_path>+0x53
> 00000069`f24ffcb0 00007ff6`33f0df8a : 000001b4`4d42b3e0
> 00000000`00000000 000001b4`4d42b3e0 00000000`00000000 :
> cytiva_aktaflux!boost::asio::error::`dynamic initializer for
> 'misc_category''+0x14
> 00000069`f24ffe40 00007ffc`2fe8268a : 00000000`00000000
> 000001b4`4d287670 00000000`00000000 00000000`00000000 :
> cytiva_aktaflux!boost::exception_detail::current_exception_std_exception<std::underflow_error>+0x9a
> 00000069`f24ffe70 00007ffc`32917ad4 : 00000000`00000000
> 00000000`00000000 00000000`00000000 00000000`00000000 :
> ucrtbase!thread_start<unsigned int (__cdecl*)(void * __ptr64)>+0x3a
> 00000069`f24ffea0 00007ffc`333aa371 : 00000000`00000000
> 00000000`00000000 00000000`00000000 00000000`00000000 :
> kernel32!BaseThreadInitThunk+0x14
> 00000069`f24ffed0 00000000`00000000 : 00000000`00000000
> 00000000`00000000 00000000`00000000 00000000`00000000 :
> ntdll!RtlUserThreadStart+0x21
>
> Best Regards,
> Jyotideep (JD)
> Please be advised that this email may contain confidential information.
> If you are not the intended recipient, please notify us by email by
> replying to the sender and delete this message. The sender disclaims
> that the content of this email constitutes an offer to enter into, or
> the acceptance of, any agreement; provided that the foregoing does not
> invalidate the binding effect of any digital or other electronic
> reproduction of a manual signature that is included in any attachment.
>
> Confidential - Company Proprietary
>
>
> _______________________________________________
> Unsubscribe & other changes: https://urldefense.com/v3/__http://lists.boost.org/mailman/listinfo.cgi/boost__;!!G8Er-fQLpA!PFdqC80cipChB5rIkDH1aktGE0i6XEEjdFsAZu85skLdRBti21XVgU7V68UMon1l2Z7yNyDxDNa4EfQgPUSdv5Z3$
>
> Attachments:
> * windbg.txt
_______________________________________________
Unsubscribe & other changes: https://urldefense.com/v3/__http://lists.boost.org/mailman/listinfo.cgi/boost__;!!G8Er-fQLpA!PFdqC80cipChB5rIkDH1aktGE0i6XEEjdFsAZu85skLdRBti21XVgU7V68UMon1l2Z7yNyDxDNa4EfQgPUSdv5Z3$
Please be advised that this email may contain confidential information. If you are not the intended recipient, please notify us by email by replying to the sender and delete this message. The sender disclaims that the content of this email constitutes an offer to enter into, or the acceptance of, any agreement; provided that the foregoing does not invalidate the binding effect of any digital or other electronic reproduction of a manual signature that is included in any attachment.